Backups Done Right with Restic
... or at least good enough!
Restic (https://restic.net/ ) is a modern backup program designed to back up your files. Written in Go, it can be compiled and used on Linux, Windows, macOS, and BSD systems. Restic features end-to-end encryption, supports a wide range of storage backends, and includes deduplication for backed-up files.
I use Restic nightly to back up my cloud servers, ensuring that the last 30 days' worth of data is always accessible in case of data loss. Here’s how I set it up and why I believe it's secure and reliable enough for most normal use cases. My setup includes multiple cloud servers hosted by Netcup (https://www.netcup.com ) and a small homelab with several terabytes of storage.
On the homelab server, I run Restic’s REST server (https://github.com/restic/rest-server ), which offers an HTTP API for the Restic client to upload data.
Why Use the Restic REST Server?
The primary advantage of using Restic's REST server over other backends is its support for append-only mode. This feature ensures that once data is uploaded, it cannot be deleted or altered, minimizing risks associated with potential security breaches.
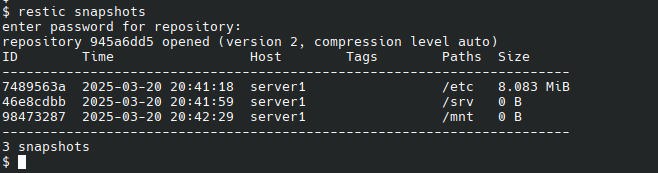
Restic Rest-Server setup
I use Docker and Docker Compose on all my servers to orchestrate and install software. Here’s my docker-compose.yml file for setting up the Restic REST server:
version: "2"
services:
restic-server:
image: restic/rest-server:latest
restart: unless-stopped
environment:
- OPTIONS=--append-only --private-repos
volumes:
- /mnt/raid/restic-server:/data:rw
networks:
- frp
networks:
frp:
external: trueBy default, the Restic REST server uses a .htaccess file in the /data directory to enable basic authentication for API endpoints.
Making It Available from Outside
To make my homelab services accessible from outside, I use FRP (https://github.com/fatedier/frp ) as a reverse proxy. On the homelab side, I run an FRP client inside a Docker container:
version: "3"
services:
frp:
image: snowdreamtech/frpc:latest
restart: "unless-stopped"
volumes:
- "./frpc.toml:/etc/frp/frpc.toml:ro"
networks:
- frp
networks:
frp:
name: frp
external: trueThe frpc.toml configuration file lists the endpoints to be proxied:
serverAddr = "example.com"
serverPort = 1234
auth.method = "token"
auth.token = "abc123"
[[proxies]]
name = "restic"
type = "tcp"
remotePort = 3078
localPort = 8000
localIp = "restic-server"
transport.useEncryption = true
transport.useCompression = trueOn one of the cloud servers, I run an FRP server that exposes services via Traefik (a reverse proxy). Here’s a Docker Compose file for setting up the FRP server:
version: '2'
services:
frps:
image: snowdreamtech/frps:latest
ports:
- "1234:1234/tcp"
- "1234:1234/udp"
restart: "unless-stopped"
user: 1001:1001
labels:
- "traefik.enable=true"
- "traefik.http.routers.relay-restic.rule=Host(`restic.example.com`)"
- "traefik.http.routers.relay-restic.entrypoints=websecure"
- "traefik.http.routers.relay-restic.tls.certresolver=le"
- "traefik.http.routers.relay-restic.service=relay-restic"
- "traefik.http.services.relay-restic.loadbalancer.server.port=3078"
- "traefik.docker.network=traefik-pub"
volumes:
- "./frps.toml:/frps.toml:ro"
command: "-c /frps.toml"
networks:
- traefik-pub
networks:
traefik-pub:
external: trueThe traefik-pub network is configured within the Traefik Docker Compose stack and encapsulates all web services made available by Traefik. I'll not go into detail here on how to configure traefik with lets encrypt and https.
The corresponding frps.toml looks like this:
bindPort = 1234
auth.method = "token"
auth.token = "abc123"
transport.tls.force = trueSetting Up the Restic Client
To perform backups, I use the Restic CLI. A cron job invokes the backup script nightly:
#!/bin/bash
source ./homelab.env
## Backing up basic configs
restic backup /srv
restic backup /etc
...The homelab.env file contains the endpoint and credentials for the reverse-proxied Restic REST server:
#!/bin/bash
export RESTIC_REPOSITORY=rest:https://user:pass@restic.example.com/server1/
export RESTIC_PASSWORD="encryption-key"The RESTIC_PASSWORD is used to end-to-end encrypt backup data.
Managing Backup Retention
To manage retention policies, I run a cron job nightly on the homelab server that uses --keep-within 30d to remove snapshots older than 30 days:
export RESTIC_REPOSITORY="/mnt/raid/restic-server/server1"
export RESTIC_PASSWORD="encryption-key"
restic forget --keep-within 30d --pruneThis setup ensures that my backups are both secure and reliable, providing peace of mind for data protection.